How to setup OpenVPN Server?
What is OpenVPN?
OpenVPN is a virtual private network (VPN) system that implements technology to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It implements client and server applications.
OpenVPN Server refers to the computer or device running the OpenVPN service. The role of an OpenVPN server is to allow client devices to connect to their own private network over the Internet or other networks and establish a secure communication link.
How does OpenVPN work?
Set up OpenVPN Server on wavlink router
1 . Enter the IP address of the device management interface in the browser address bar, log in to the management interface, click More Settings, and enter OpenVPN Server.
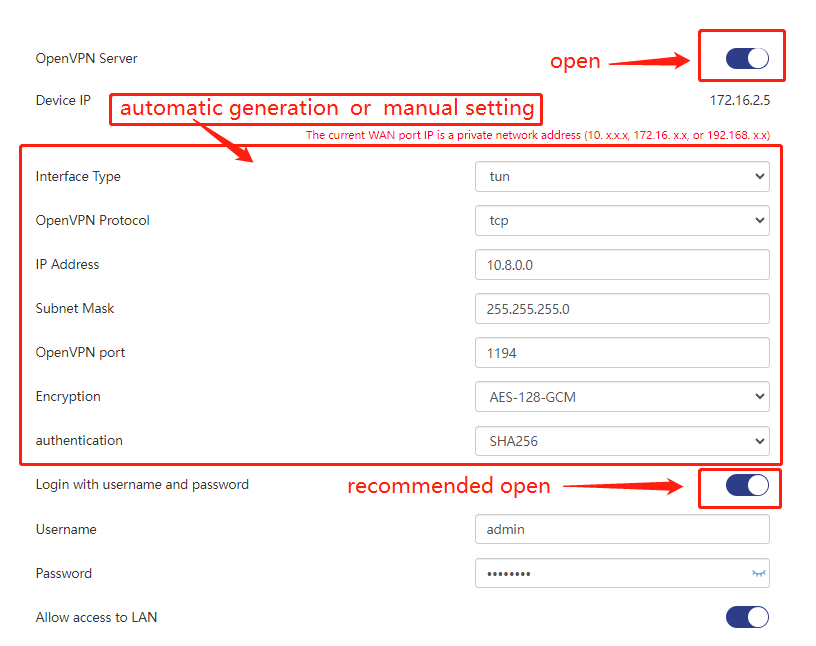
2 . To configure OpenVPN Server, you can choose to automatically generate or configure it manually. You can refer to the following two methods to complete the configuration of your own OpenVPN Server. If you are new to this, it is recommended that you use automatic generation.
Click to start OpenVPN Server, and the device will automatically generate OpenVPN Server configuration information.It is recommended that you enable login user and password to improve security.
Info
The network segments of OpenVPN Server and OpenVPN Client cannot be the same. If the client and server use the same IP network segment, network conflicts may occur and data cannot be transmitted correctly.
If you do not want to use the system configuration, you can click the parameter corresponding box to customize the settings.It is recommended that you enable login user and password to improve security.
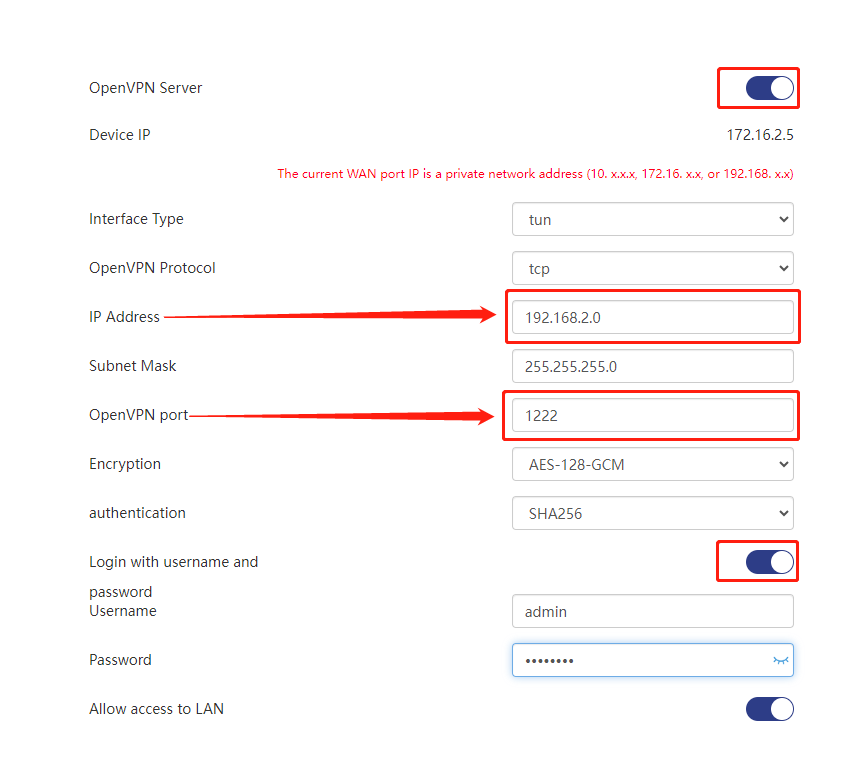
The parameters in the figure can be set according to your needs, but you need to pay attention to the usable range of the parameters. We have listed the meaning and applicable range of each parameter for you.
TUN means using a virtual tunnel interface. This means that OpenVPN will create a virtual network interface (e.g. tun0) and transmit the encrypted data stream through this interface.
TAP means using a virtual Ethernet adapter. This means that OpenVPN will create a virtual network interface (e.g. tap0) and transmit the encrypted data stream through this interface. Unlike the tun interface, the tap interface can transmit Ethernet frames rather than just IP packets.

TAP devices work exactly the same as TUN devices, with the following differences :
-
The TUN device cannot bridge with the physical network card, but it can be connected to the physical network card through Layer 3 switching.
-
TAP devices can bridge with physical network cards and support MAC layer broadcast.(If you need to use bridging, select TAP.)
OpenVPN can run on two different transport layer protocols: TCP and UDP. The choice of which protocol to use often depends on your specific network needs and environment.

UDP protocol is suitable for the following situations:
Speed and efficiency : UDP is a connectionless protocol that does not require a connection to be established at the beginning of communication like TCP, so it is generally faster and more efficient than TCP when transferring data.
Real-time requirements : For applications that require fast data transmission and can tolerate a certain degree of packet loss, such as online games, voice calls, etc., UDP can better meet the needs.
Lower requirements for data integrity : UDP does not provide a packet retransmission and acknowledgment mechanism, so UDP can be chosen when there are lower requirements for data packet integrity.
TCP protocol is suitable for the following situations :
High reliability requirements : Compared with UDP, TCP provides a reliable data transmission mechanism, including retransmission and confirmation of data packets, so it is suitable for scenarios with high data integrity requirements.
Firewall penetration : In some network environments, UDP may be restricted by firewalls, and TCP communications are more likely to penetrate firewalls in these network environments.
High data transmission stability requirements : For scenarios such as file transfer that require high data transmission stability, you can choose to use TCP.
Generally speaking, UDP can usually be selected when data needs to be transmitted quickly, real-time requirements are high, or data integrity requirements are not so strict;TCP can be selected when data integrity requirements are high, reliable data transmission is required, or firewall penetration is required.
The IP address uses a private network address. We have listed the following private network addresses for you. You can choose according to your needs.

The private network address is:
- Class A address: 10.0.0.0~10.255.255.255
- Class B address: 172.16.0.0 ~ 172.31.255.255
- Class C address: 192.168.0.0~192.168.255.255
Info
The network segments of OpenVPN Server and OpenVPN Client cannot be the same. If the client and server use the same IP network segment, network conflicts may occur and data cannot be transmitted correctly.
255.255.255.0 means that the OpenVPN server will use a 24-bit subnet mask. This means that the OpenVPN server will assign the VPN client an IP address of the form 192.168.20.x, where x ranges from 1 to 254.

Depending on your network environment and needs, the subnet mask settings may vary. Make sure you take into account factors such as network size, performance needs and security when making any changes.
The default port used by OpenVPN is 1194/UDP. Of course, you can also customize the port range in the OpenVPN configuration. If port forwarding is required through a firewall or router, or the default port needs to be modified for security reasons, you can select other ports for configuration. Generally speaking, you can choose any port that is not occupied by other services as the port range for OpenVPN, but please make sure that the corresponding firewall and router are set accordingly during configuration.

The available range of port numbers is from 0 to 65535. However, some of these port numbers have been standardized as default ports used by specific protocols or services, so it is not recommended to select these ports in this range. Here are some common port number ranges:
Well-known Ports: From 0 to 1023, these port numbers are usually used for standardized services and protocols, such as HTTP (port number 80), HTTPS (port number 443), FTP (port number 21), etc.
Registered Ports: From 1024 to 49151, these port numbers are used by applications and services developed by third parties but are not officially standardized.
Dynamic and/or Private Ports: From 49152 to 65535, these port numbers are for temporary allocation or internal use and are generally not assigned to a specific service or protocol.
When selecting a port range, it is recommended to avoid using ports that are already occupied by commonly used protocols or services to prevent conflicts and confusion. You can choose to configure it within a registered port or a dynamic/private port range to ensure there is no conflict with other services, and make appropriate network configuration and security settings as needed.
Each encryption method has its own characteristics and applicable scenarios. You can choose the appropriate encryption method according to your specific needs.
For example, if you are pursuing higher performance, you can consider using the AES encryption algorithm in GCM mode; if you need to balance performance and security, you can consider the CHACHA20-POLY1305 algorithm.
-
AES-256-GCM: This is the AES symmetric encryption algorithm using a 256-bit key length, combined with GCM mode for encryption. GCM mode provides authentication and encryption and has better performance than CBC mode.
-
AES-128-GCM: Similar to above, but uses the AES symmetric encryption algorithm with a 128-bit key length.
-
AES-128-CBC: This is the AES symmetric encryption algorithm using a 128-bit key length, combined with CBC mode for encryption. CBC mode is a common block encryption mode, but it is slightly inferior in performance compared to GCM mode.
-
CHACHA20-POLY1305: This is a combination of ChaCha20 encryption algorithm and Poly1305 message authentication code for high performance and security.

SHA-256 and SHA-51__2 are both hash algorithms in the __SHA-2 (Secure Hash Algorithm 2) family. The main difference between them is the output length and computational complexity :
-
Output length: SHA-256 produces a hash value of 256 bits (32 bytes), while SHA-512 produces a hash value of 512 bits (64 bytes). Therefore, SHA-512 provides a longer hash value and is theoretically more collision resistant.
-
Computational complexity: Since the hash value generated by SHA-512 is longer, calculating the SHA-512 hash value requires more computing resources and time compared to SHA-256. This means that SHA-512 may be calculated slightly slower than SHA-256.
-
Security: Although both SHA-256 and SHA-512 are widely used and no effective attack method has been found yet, the longer output length of SHA-512 means higher security. Longer hash values increase the difficulty of collisions, making it more difficult to find two different inputs that produce the same hash value through an attack.

Choose the appropriate hash algorithm according to different security needs and performance requirements. Normally, for most applications, SHA-256 is sufficient to meet security requirements, its output length is short, and its calculation speed is relatively fast. Under specific security needs, or when there is a higher requirement for higher collision resistance, you can choose SHA-512.
Username and Password Login,indicates that authentication with a username and password is required to allow the client to connect to the VPN server.

3 . Click Save and wait for the application to be updated.
4 . After the application is successful, the Export Configuration File and Export Log File will appear on the settings page.
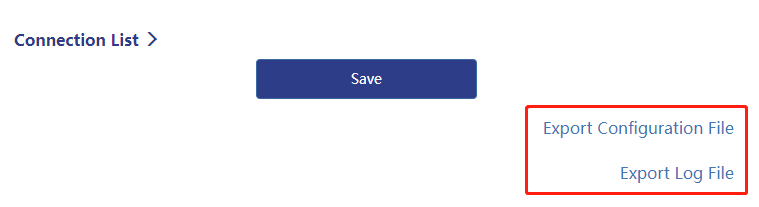
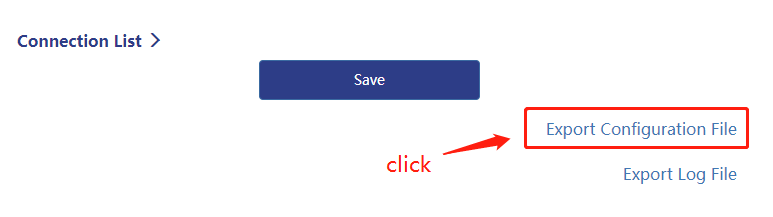
5 . Click Export Configuration File to automatically generate and download the OpenVPN Server configuration file (the file suffix is .ovpn). Please remember the location of the configuration file, which is required when the OpenVPN Client connects to the OpenVPN Server.
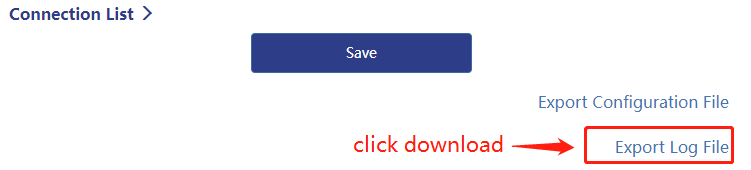
6 . If the client connection fails, you can click Export Log File to download the log and view the reason for the failure.
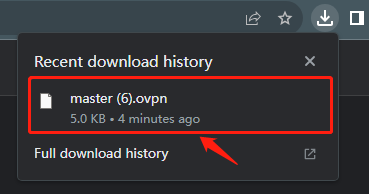
7 . After downloading, you can click the download icon to view it.
Application scenarios
Remote Access : OpenVPN can be used as a remote access solution, allowing users to securely access internal company resources over untrusted networks. Employees can connect to the corporate network through OpenVPN and access files, applications, and internal systems without having to connect directly to the company's LAN.
Site-to-site connections : OpenVPN can be used to establish secure site-to-site connections, enabling secure communication between networks in different locations. This is useful for businesses that span multiple offices or branch offices, allowing for secure data transfer and resource sharing.
Enhanced WiFi security : Public WiFi hotspots often present security risks, and using OpenVPN can enhance the security of your connection. By connecting to an OpenVPN server, users can establish an encrypted connection over an untrusted network, protecting their data from hackers or eavesdroppers.
Encrypted data transfer : OpenVPN can be used as a solution for encrypted data transfer. If you need to transmit sensitive data over an unsecured network, using OpenVPN can ensure the confidentiality and integrity of your data, preventing it from being stolen or tampered with.
Surf the Internet Anonymously : By connecting to an OpenVPN server, you can hide your real IP address and surf the Internet through the server’s IP address. This can help protect your privacy and prevent your online activities from being tracked.
These are just some common usage scenarios, and OpenVPN's flexibility allows it to adapt to a variety of security needs and network configurations. Whether for individual users or businesses, OpenVPN can provide secure remote access and data transfer solutions.